Browsers' Insecure Password Storage

Everyone I know has stored passwords in their browser at least once. Regardless of your browser of choice, this is not a wise decision. Much like TSA, all there is to be seen is security theater.
The average user assumes the safety of using the browser storage - why else would Apple/Google/Mozilla/etc. offer the feature? Attempting to reveal the password will prompt for the system password or for biometric identification, after all.
However, there's a fundamental problem with the logic behind the password management. A user is not required to copy/paste the credentials into a given website; the credentials are autocompleted. A quick modification to the DOM and your password has been compromised.
Here you can see the standard Google login page with the password field in focus:
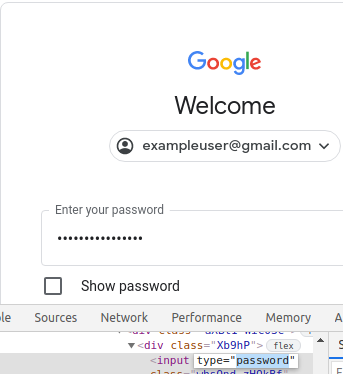
A quick change from type="password" to type="text" will yield the password:
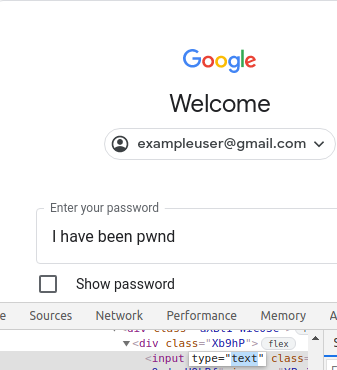
Ultimately, the password page in a browser acts as an index for the websites that can be compromised. Modifying the DOM on a website gives an attacker instant access to the credentials. The only safety at that point is two-factor authentication.
Unlocking the browser itself with a password is an interesting thought. However, we would just be reinventing the wheel; use a password manager.
